ポッドキャスト収録用のメモですよ。
podcast - #セキュリティのアレ - ゆるーいセキュリティのポッドキャストですよ。
- 事件、事故
- 攻撃、脅威
- NCSC からランサムウェアを取り巻くエコシステムに関する報告
- Microsoft が攻撃者グループ Storm-0324 による攻撃活動について報告
- Symantec が攻撃者グループ Redfly によるアジアの国の送電網を狙う攻撃活動について報告
- Chainalysis が北朝鮮による暗号資産を狙う攻撃活動について報告
- Mandiant が攻撃者グループ UNC3944 による攻撃活動について報告
- Microsoft が攻撃者グループ Peach Sandstorm による攻撃活動について報告
- JPCERT/CC が Array Networks Array AGシリーズの脆弱性を悪用する攻撃活動に関する注意喚起
- 脆弱性
- CISA が Known Exploited Vulnerabilities (KEV) カタログに 2+2+3+1 個の脆弱性を追加
- Apple が macOS Monterey 12.6.9, macOS Big Sur 11.7.10, iOS 15.7.9 / iPadOS 15.7.9 をリリース。すでに悪用が確認されている脆弱性の修正を含む
- WebP ライブラリに脆弱性があり、Chrome や Firefox など複数の製品に影響。すでに悪用が確認されている
- Microsoft が 2023年 9月の月例パッチを公開。すでに悪用が確認されている複数の脆弱性を含む。
- Adobe Acrobat および Reader の脆弱性が修正。すでに悪用が確認されている。
- その他
事件、事故
暗号資産取引所 CoinEx から不正アクセスによる資金流出
(9/13) Hackers steal $53 million worth of cryptocurrency from CoinEx
Urgent Notice: Security Incident on CoinEx - Immediate Actions Underway
— CoinEx Global (@coinexcom) September 12, 2023
On September 12, 2023, our Risk Control System detected anomalous withdrawals from several hot wallet addresses used to store CoinEx's exchange assets. Promptly recognizing the gravity of the situation, we…
アイルランドのデータ保護委員会が TikTok に対して GDPR 違反による 3億4500万ユーロの罰金を科すと発表
攻撃、脅威
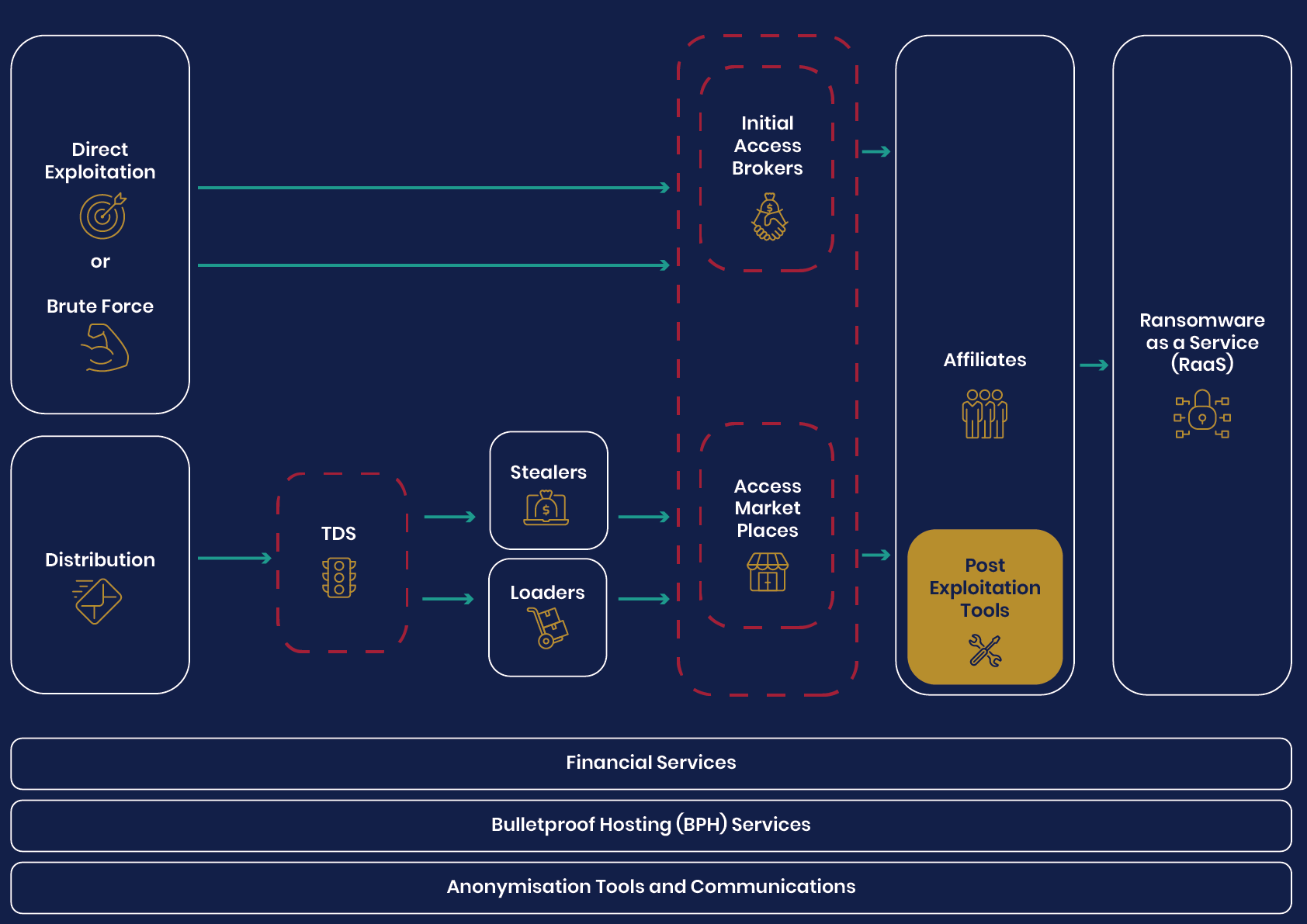
NCSC からランサムウェアを取り巻くエコシステムに関する報告
(9/11) Ransomware, extortion and the cyber crime ecosystem - NCSC.GOV.UK
This white paper has illustrated how ransomware and extortion attacks reflect a diverse and varied business model, that's reliant on a complex supply chain. Focussing on specific ransomware strains can be confusing at best, and unhelpful at worst. Most ransomware incidents are not due to sophisticated attack techniques; the initial accesses to victims are gained opportunistically, with success usually the result of poor cyber hygiene. Implementing the NCSC guidance listed below would interrupt the majority of attacks.
Microsoft が攻撃者グループ Storm-0324 による攻撃活動について報告
(9/12) Malware distributor Storm-0324 facilitates ransomware access | Microsoft Security Blog
The threat actor that Microsoft tracks as Storm-0324 is a financially motivated group known to gain initial access using email-based initial infection vectors and then hand off access to compromised networks to other threat actors. These handoffs frequently lead to ransomware deployment. Beginning in July 2023, Storm-0324 was observed distributing payloads using an open-source tool to send phishing lures through Microsoft Teams chats. This activity is not related to the Midnight Blizzard social engineering campaigns over Teams that we observed beginning in May 2023. Because Storm-0324 hands off access to other threat actors, identifying and remediating Storm-0324 activity can prevent more dangerous follow-on attacks like ransomware.
Symantec が攻撃者グループ Redfly によるアジアの国の送電網を狙う攻撃活動について報告
(9/12) Redfly: Espionage Actors Continue to Target Critical Infrastructure | Symantec Enterprise Blogs
Espionage actors are continuing to mount attacks on critical national infrastructure (CNI) targets, a trend that has become a source of concern for governments and CNI organizations worldwide. Symantec’s Threat Hunter Team has found evidence that a threat actor group Symantec calls Redfly used the ShadowPad Trojan to compromise a national grid in an Asian country for as long as six months earlier this year. The attackers managed to steal credentials and compromise multiple computers on the organization’s network.
The attack is the latest in a series of espionage intrusions against CNI targets. In May 2023, the U.S., UK, Australian, Canadian, and New Zealand governments issued a joint alert about threat actors targeting CNI organizations in the U.S. using techniques that could potentially be replicated against targets in other countries. The alert followed Microsoft’s report on Volt Typhoon, an espionage actor that compromised several critical infrastructure organizations in the U.S.
Chainalysis が北朝鮮による暗号資産を狙う攻撃活動について報告
While the shift in laundering strategy illuminates new complexities, hacking activities associated with DPRK in general show a paradoxical trend as we approach the end of the third quarter. According to Chainalysis data, the value of stolen cryptocurrency associated with DPRK groups currently exceeds $340.4 million this year, compared to over $1.65 billion in stolen funds reported in 2022.
Mandiant が攻撃者グループ UNC3944 による攻撃活動について報告
UNC3944 is a financially motivated threat cluster that has persistently used phone-based social engineering and SMS phishing campaigns (smishing) to obtain credentials to gain and escalate access to victim organizations. At least some UNC3944 threat actors appear to operate in underground communities, such as Telegram and underground forums, which they may leverage to acquire tools, services, and/or other support to augment their operations. This activity overlaps with activity that has been reported in open sources as "0ktapus," "Scatter Swine," and "Scattered Spider." Since 2022 and through early 2023, UNC3944 appeared to focus on accessing credentials or systems used to enable SIM swapping attacks, likely in support of secondary criminal operations occurring outside of victim environments. However, in mid-2023, UNC3944 began to shift to deploying ransomware in victim environments, signaling an expansion in the group's monetization strategies. These changes in their end goals signal that the industries targeted by UNC3944 will continue to expand; Mandiant has already directly observed their targeting broaden beyond telecommunication and business process outsourcer (BPO) companies to a wide range of industries including hospitality, retail, media and entertainment, and financial services.
Microsoft が攻撃者グループ Peach Sandstorm による攻撃活動について報告
Since February 2023, Microsoft has observed password spray activity against thousands of organizations carried out by an actor we track as Peach Sandstorm (HOLMIUM). Peach Sandstorm is an Iranian nation-state threat actor who has recently pursued organizations in the satellite, defense, and pharmaceutical sectors around the globe. Based upon the profile of victim organizations targeted and the observed follow-on intrusion activity, Microsoft assesses that this initial access campaign is likely used to facilitate intelligence collection in support of Iranian state interests.
JPCERT/CC が Array Networks Array AGシリーズの脆弱性を悪用する攻撃活動に関する注意喚起
(9/14) Array Networks Array AGシリーズの脆弱性を悪用する複数の標的型サイバー攻撃活動に関する注意喚起
JPCERT/CCでは、2022年5月以降、サイバーセキュリティ協議会の活動などを通じて、Array Networks Array AGシリーズの脆弱性を悪用したと思われる複数の標的型サイバー攻撃を断続的に確認しています。後述のとおり、複数の攻撃グループ/攻撃活動が本製品の脆弱性を悪用していると考えられ、また、国内のみならず海外拠点も標的となっているため、自組織の海外拠点における対策や侵害有無の調査も推奨します。
攻撃活動が確認され始める前後および期間中には、本製品において、次の脆弱性が公表および修正されています。
- CVE-2022-42897(2022年4月公表、9月修正)
- CVE-2023-28461(2023年3月公表、同月修正)
脆弱性
CISA が Known Exploited Vulnerabilities (KEV) カタログに 2+2+3+1 個の脆弱性を追加
(9/11) CISA Adds Two Known Vulnerabilities to Catalog | CISA
(9/12) CISA Adds Two Known Vulnerabilities to Catalog | CISA
- CVE-2023-36761 Microsoft Word Information Disclosure Vulnerability
- CVE-2023-36802 Microsoft Streaming Service Proxy Elevation of Privilege Vulnerability
(9/13) CISA Adds Three Known Vulnerabilities to Catalog | CISA
- CVE-2023-35674 Android Framework Privilege Escalation Vulnerability
- CVE-2023-20269 Cisco Adaptive Security Appliance and Firepower Threat Defense Unauthorized Access Vulnerability
- CVE-2023-4863 Google Chrome Heap-Based Buffer Overflow Vulnerability
(9/14) CISA Adds One Known Vulnerability to Catalog | CISA
- CVE-2023-26369 Adobe Acrobat and Reader Out-of-Bounds Write Vulnerability
Apple が macOS Monterey 12.6.9, macOS Big Sur 11.7.10, iOS 15.7.9 / iPadOS 15.7.9 をリリース。すでに悪用が確認されている脆弱性の修正を含む
(9/11) Apple security releases - Apple Support
WebP ライブラリに脆弱性があり、Chrome や Firefox など複数の製品に影響。すでに悪用が確認されている
(9/11) Chrome Releases: Stable Channel Update for Desktop
Critical CVE-2023-4863: Heap buffer overflow in WebP. Reported by Apple Security Engineering and Architecture (SEAR) and The Citizen Lab at The University of Torontoʼs Munk School on 2023-09-06
(9/12) Chrome Releases: Stable Channel Update for Desktop
(9/12) NVD - CVE-2023-4863
(9/14) WebPコーデックの重大な脆弱性対処でChromeなど主要Webブラウザが緊急更新 - ITmedia NEWS
Microsoft が 2023年 9月の月例パッチを公開。すでに悪用が確認されている複数の脆弱性を含む。
(9/12) 2023 年 9 月のセキュリティ更新プログラム (月例) | MSRC Blog | Microsoft Security Response Center
今月のセキュリティ更新プログラムで修正した脆弱性のうち、以下の脆弱性は更新プログラムが公開されるよりも前に悪用や脆弱性の詳細が一般へ公開されていることを確認しています。お客様においては、更新プログラムの適用を早急に行ってください。脆弱性の詳細は、各 CVE のページを参照してください。
(9/12) Zero Day Initiative — The September 2023 Security Update Review
Adobe Acrobat および Reader の脆弱性が修正。すでに悪用が確認されている。
(9/12) Security update available for Adobe Acrobat and Reader | APSB23-34
Adobe has released a security update for Adobe Acrobat and Reader for Windows and macOS. This update addresses a critical vulnerability. Successful exploitation could lead to arbitrary code execution .
Adobe is aware that CVE-2023-26369 has been exploited in the wild in limited attacks targeting Adobe Acrobat and Reader.
その他
米国土安全保障省 (DHS) が "Homeland Threat Assessment 2024" を公開
(9/13) Homeland Threat Assessment | Homeland Security
NTT セキュリティが「サイバーセキュリティレポート 2023.08」を公開
(9/14) サイバーセキュリティレポート 2023年8月