ポッドキャスト収録用のメモですよ。
podcast - #セキュリティのアレ - ゆるーいセキュリティのポッドキャストですよ。
事件、事故
国内の複数の Web サイトで改ざん被害
(9/4) 公式サイトに「破産した」の偽情報 改ざんの被害続々 研修施設、コンサルなどで - ITmedia NEWS
公式Webサイトが改ざんされ「破産した」などの偽情報を載せられたとする被害の報告が、8月31日から9月4日にかけて相次いでいる。いずれも実際には破産しておらず、事態の確認・調査を進めている。被害の関連性は不明。
(9/6) acmailerの脆弱性にご注意ください | さくらのサポート情報
#注意喚起 🚨
— piyokango (@piyokango) September 4, 2023
国内でWebサイト改ざんが頻発していますが、acmailerの既知の脆弱性を悪用し侵入されている可能性があります。
最新版へ更新しているか、更新していない場合は認証情報の改ざんや不正プログラム設置等の影響を受けていないか、確認されることを推奨します。https://t.co/TGgDfZBAnD
トヨタが先月末に発生した生産指示システムの不具合について、原因は作業用のディスク容量不足だったと報告
(9/6) 先月の生産指示システムの不具合について | コーポレート | グローバルニュースルーム | トヨタ自動車株式会社 公式企業サイト
今回のシステム不具合は、部品の発注処理を行う複数のサーバーの一部が利用できなくなったことで発生しました。経緯としては、不具合発生の前日8月27日に定期の保守作業を実施しました。この保守作業では、データベースに溜まったデータの削除と整理を行っておりましたが、作業用のディスク容量が不足していたためエラーが発生し、それによってシステムが停止いたしました。これらのサーバーは、同一のシステムで作動していたため、バックアップ機でも同様の障害が発生し切り替えができず、工場の稼動停止に至りました。その後、8月29日に容量の大きいサーバーにデータを移管したことで、システムが復旧し、工場稼働を再開いたしました。この度、再現検証によって、上記が真因・その対策となることを特定しましたのでご報告いたします。
(参考) 保守作業中のディスク容量不足で発生したトヨタ国内全工場の稼働停止についてまとめてみた - piyolog
JTB の元従業員が顧客のクレジットカードを不正利用した電子計算機使用詐欺罪の容疑で逮捕
(9/7) 「JTB旅物語中部販売センター」元従業員の不祥事に関するお詫び|ニュースルーム|JTBグループサイト
(9/7) クレジットカード情報不正利用し「投げ銭」購入した疑いで逮捕|NHK 東海のニュース
米司法省が Trickbot マルウェアおよび Conti ランサムウェアの活動に関与した複数のロシア人を起訴
According to court documents and public reporting, Trickbot, which was taken down in 2022, was a suite of malware tools designed to steal money and facilitate the installation of ransomware. Hospitals, schools, and businesses were among the millions of Trickbot victims who suffered tens of millions of dollars in losses. While active, Trickbot malware, which acted as an initial intrusion vector into victim computer systems, was used to support various ransomware variants, including Conti. Conti was a ransomware variant used to attack more than 900 victims worldwide, including victims in approximately 47 states, the District of Columbia, Puerto Rico, and approximately 31 foreign countries. According to the FBI, in 2021, Conti ransomware was used to attack more critical infrastructure victims than any other ransomware variant.
Today, the United States, in coordination with the United Kingdom, sanctioned eleven individuals who are part of the Russia-based Trickbot cybercrime group. Russia has long been a safe haven for cybercriminals, including the Trickbot group. Today’s action was taken by the U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC). The U.S. Department of Justice (DOJ) is concurrently unsealing indictments against nine individuals in connection with the Trickbot malware and Conti ransomware schemes, including seven of the individuals designated today.
攻撃、脅威
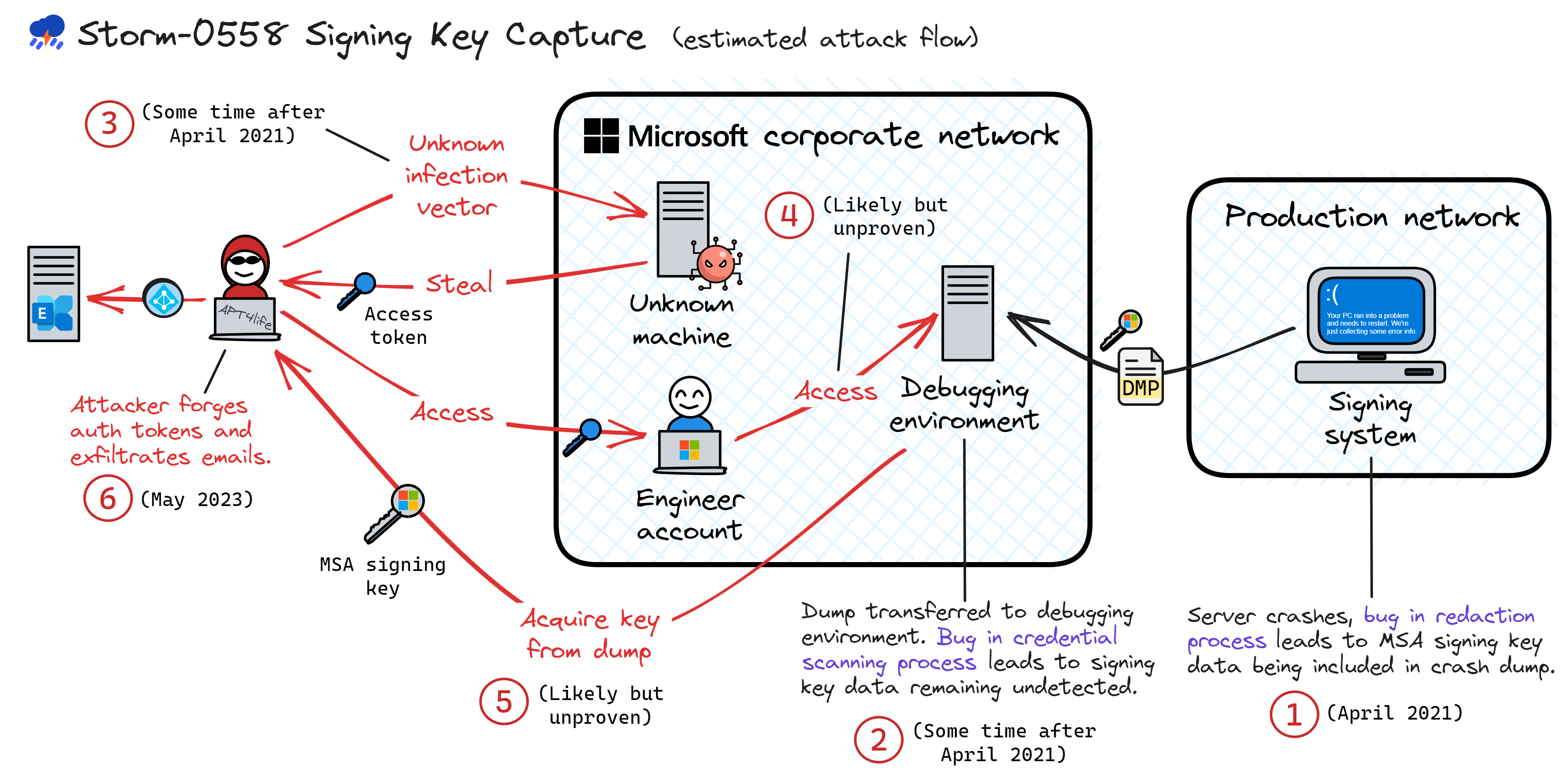
Microsoft が 7月に報告した中国の攻撃者グループ Storm-0558 による攻撃活動に関する続報
(9/7) Storm-0558 Update: Takeaways from Microsoft's recent report | Wiz Blog
CISA、FBI、CNMF が共同で、複数の国家を背景とする攻撃者グループによる攻撃活動に関する注意喚起
(9/7) Multiple Nation-State Threat Actors Exploit CVE-2022-47966 and CVE-2022-42475 | CISA
The Cybersecurity and Infrastructure Security Agency (CISA), Federal Bureau of Investigation (FBI), and Cyber National Mission Force (CNMF) identified the presence of indicators of compromise (IOCs) at an Aeronautical Sector organization as early as January 2023. Analysts confirmed that nation-state advanced persistent threat (APT) actors exploited CVE-2022-47966 to gain unauthorized access to a public-facing application (Zoho ManageEngine ServiceDesk Plus), establish persistence, and move laterally through the network. This vulnerability allows for remote code execution on the ManageEngine application. Additional APT actors were also observed exploiting CVE-2022-42475 to establish presence on the organization’s firewall device.
Google が北朝鮮の攻撃者グループによるセキュリティ研究者を狙う攻撃活動について報告
(9/7) Active North Korean campaign targeting security researchers
In January 2021, Threat Analysis Group (TAG) publicly disclosed a campaign from government backed actors in North Korea who used 0-day exploits to target security researchers working on vulnerability research and development. Over the past two and a half years, TAG has continued to track and disrupt campaigns from these actors, finding 0-days and protecting online users. Recently, TAG became aware of a new campaign likely from the same actors based on similarities with the previous campaign. TAG is aware of at least one actively exploited 0-day being used to target security researchers in the past several weeks. The vulnerability has been reported to the affected vendor and is in the process of being patched.
Microsoft が中国および北朝鮮の攻撃者グループによる攻撃活動について報告
(9/7) China, North Korea pursue new targets while honing cyber capabilities - Microsoft On the Issues
脆弱性
Google が Android の複数の脆弱性を修正。すでに悪用が確認されている脆弱性を含む
(9/5) Android Security Bulletin—September 2023 | Android Open Source Project
There are indications that CVE-2023-35674 may be under limited, targeted exploitation.
ASUS 製ルーターにリモートコード実行可能な複数の脆弱性
(9/5) ASUS routers vulnerable to critical remote code execution flaws
Three critical-severity remote code execution vulnerabilities impact ASUS RT-AX55, RT-AX56U_V2, and RT-AC86U routers, potentially allowing threat actors to hijack devices if security updates are not installed.
Cisco ASA および FTD の VPN 機能にブルートフォース攻撃が可能な脆弱性。すでに悪用を確認
A vulnerability in the remote access VPN feature of Cisco Adaptive Security Appliance (ASA) Software and Cisco Firepower Threat Defense (FTD) Software could allow an unauthenticated, remote attacker to conduct a brute force attack in an attempt to identify valid username and password combinations or an authenticated, remote attacker to establish a clientless SSL VPN session with an unauthorized user.
(9/8) Cisco warns of VPN zero-day exploited by ransomware gangs
CISA が Known Exploited Vulnerabilities (KEV) カタログに 1 個の脆弱性を追加
(9/6) CISA Adds One Known Vulnerability to Catalog | CISA
- CVE-2023-33246 Apache RocketMQ Command Execution Vulnerability
Apple が macOS Ventura 13.5.2, iOS 16.6.1 / iPadOS 16.6.1, watchOS 9.6.2 をリリース。すでに悪用が確認されている 2件の脆弱性の修正を含む
(9/7) Apple security releases - Apple Support
(9/7) BLASTPASS: NSO Group iPhone Zero-Click, Zero-Day Exploit Captured in the Wild - The Citizen Lab
Last week, while checking the device of an individual employed by a Washington DC-based civil society organization with international offices, Citizen Lab found an actively exploited zero-click vulnerability being used to deliver NSO Group’s Pegasus mercenary spyware.
We refer to the exploit chain as BLASTPASS. The exploit chain was capable of compromising iPhones running the latest version of iOS (16.6) without any interaction from the victim.